Scammers are abusing PayPal’s subscription billing system to send phishing emails directly from PayPal infrastructure. The emails are sent from service@paypal.com, pass SPF, DKIM, and DMARC checks, and appear completely legitimate to recipients.
The campaign was documented by BleepingComputer after multiple people reported receiving PayPal emails stating that an automatic payment was no longer active. On its own, that message is normal. The problem appears inside the email body.
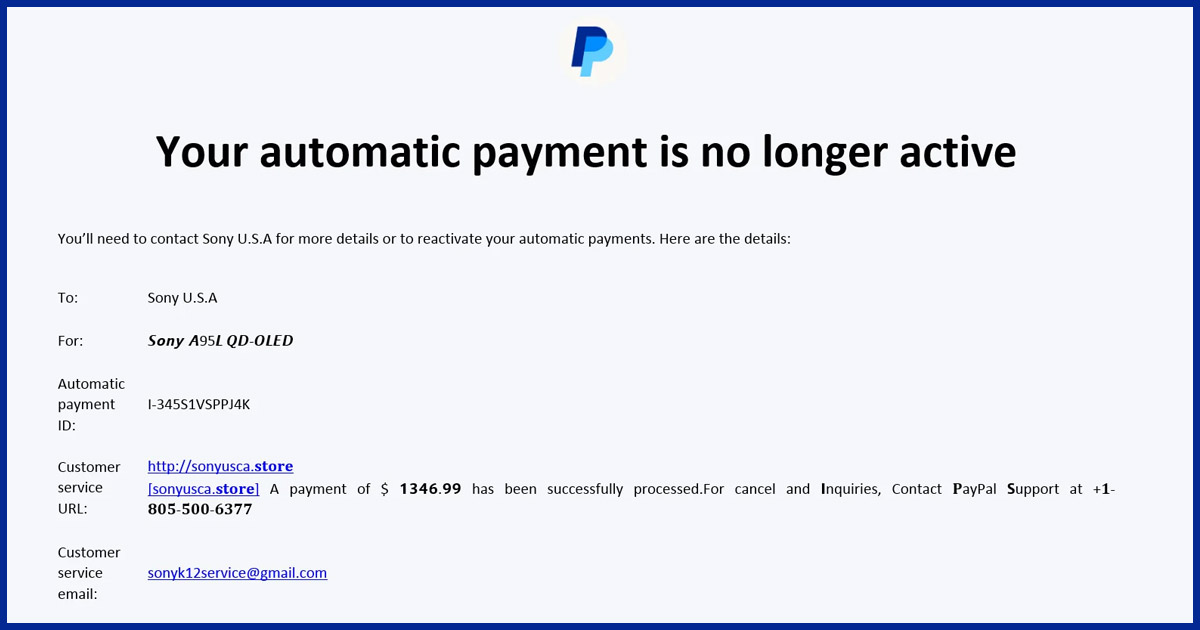
The Customer service URL field inside the email is manipulated to display a fake purchase confirmation. Instead of a support link, the field claims that an expensive item such as a MacBook, iPhone, or Sony device was purchased. The amounts typically range between 1300 and 1600 US dollars. A phone number labeled as PayPal support is included.
The fake purchase text is padded with Unicode characters that alter font weight and spacing. This makes the message visually prominent and may help it bypass spam and keyword filters.
Because the emails are sent by PayPal itself, they bypass most security filtering. Email headers confirm the messages originate from PayPal servers such as mx15.slc.paypal.com and pass all authentication checks. Recipients naturally assume their account has been compromised.
The goal is to trigger panic and push the recipient into calling the listed phone number. Once on the call, scammers attempt to steal banking details, credentials, or persuade the victim to install remote access software. This phone based fraud pattern is well established. What is new is the delivery method.
BleepingComputer tested PayPal billing features and reproduced the same email template using PayPal Subscriptions. When a merchant pauses a subscription, PayPal automatically emails the subscriber stating the automatic payment is no longer active.
Under normal conditions, the Customer service URL field only accepts valid web addresses. Attempts to insert arbitrary text are rejected. This suggests attackers are exploiting a flaw in how PayPal handles subscription metadata or using an API or legacy interface that allows invalid content to be stored.
Email headers show PayPal sends the message to an address controlled by the attacker. That address appears to be a Google Workspace mailing list which forwards the email to many recipients. This explains how people who never subscribed receive the notification.
PayPal told BleepingComputer that it is actively mitigating the method used to send these emails. No technical details were provided.
This incident shows how trusted platforms can be turned into delivery systems for fraud. When user controlled fields are reflected into system generated emails, they become an attack surface. Email authentication alone does not protect users when the content itself is abused.
Blackout VPN exists because privacy is a right. Your first name is too much information for us.
Keep learning
FAQ
Are these PayPal emails spoofed
No. The emails are sent by PayPal infrastructure and pass standard authentication checks.
What do the fake emails claim
They claim an expensive purchase was processed and urge the recipient to call a phone number.
How are scammers generating the emails
They abuse PayPal Subscriptions and manipulate fields reflected into PayPal generated emails.
Why do people receive these emails without subscribing
The emails are sent to attacker controlled mailing lists that forward them to targets.
What is the safest way to verify a PayPal charge
Log into your PayPal account directly and ignore phone numbers included in emails.