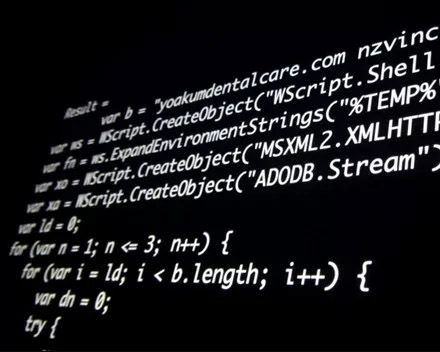
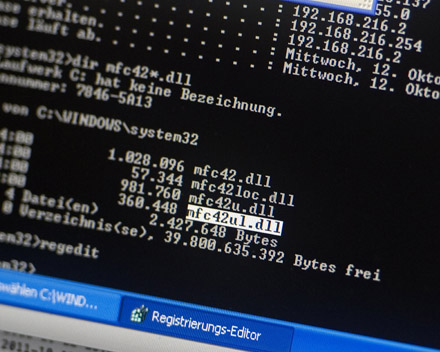
175,000 Open AI Servers Found Online With No Security
SentinelOne SentinelLABS and Censys discovered 175,000 publicly accessible Ollama AI servers operating without authentication across 130 countries. The servers form a massive unmanaged layer of AI infrastructure running outside corporate security controls.
Read more