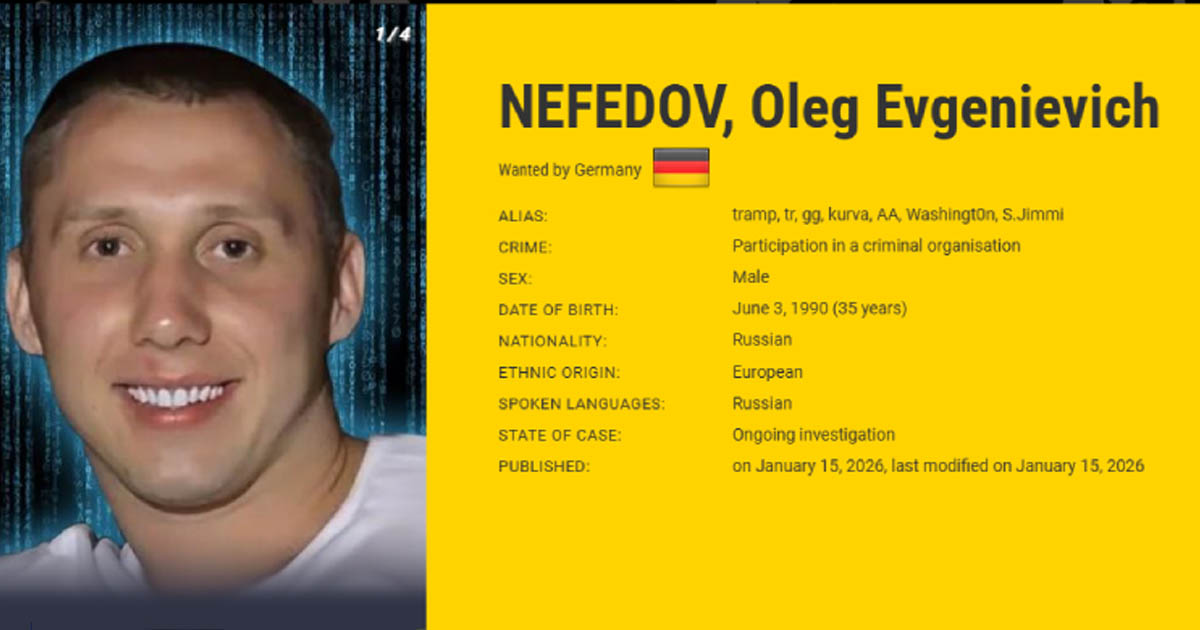
Ukrainian and German law enforcement identified the alleged leader of Black Basta ransomware as Oleg Evgenievich Nefedov, a 35-year-old Russian national. Nefedov has been added to the European Union's Most Wanted list and INTERPOL's Red Notice. Authorities also identified two Ukrainians suspected of working for the group as technical hackers who specialized in extracting passwords from protected systems.
Black Basta emerged in April 2022 and targeted more than 500 companies across North America, Europe, and Australia. The group is estimated to have earned hundreds of millions of dollars in cryptocurrency through ransom payments. A year's worth of internal chat logs from Black Basta leaked online in early 2025, exposing the group's structure, key members, and the security vulnerabilities they exploited to breach corporate networks.
The leaked chats identified Nefedov as Black Basta's leader, operating under aliases including Tramp, Trump, GG, AA, kurva, Washingt0n, and S.Jimmi. Some documents alleged Nefedov had ties to high-ranking Russian politicians and intelligence agencies including the FSB and GRU. Security firm Trellix reported that Nefedov was arrested in Yerevan, Armenia in June 2024 but secured his freedom. His current location is unknown, though he is believed to be in Russia.
Germany's Federal Criminal Police Office stated that Nefedov decided which organizations to target, recruited members, assigned tasks, participated in ransom negotiations, managed extorted funds, and paid group members. Evidence links Nefedov to Conti, a defunct ransomware group that operated from 2020 to 2022 as a successor to Ryuk. In August 2022, the US State Department announced a $10 million reward for information on five individuals associated with Conti, including someone with the alias Tramp.
The two Ukrainian suspects arrested by authorities functioned as hash crackers who extracted passwords from information systems using specialized software. After obtaining credentials, Black Basta members would breach corporate networks, deploy ransomware, encrypt data, and demand payment for decryption. Ukrainian Cyber Police conducted searches at residences in Ivano-Frankivsk and Lviv, seizing digital storage devices and cryptocurrency assets.
Black Basta appeared as an autonomous group following Conti's retirement in 2022. Other groups that emerged from Conti's shutdown include BlackByte and KaraKurt. Former Conti members also joined BlackCat, Hive, AvosLocker, and HelloKitty, all of which are now inactive.
The leaked chats led to Black Basta's apparent collapse. The group went silent after February 2025 and took down its data leak site. Security firms ReliaQuest and Trend Micro reported that several former Black Basta affiliates may have migrated to the CACTUS ransomware operation. Organizations listed on CACTUS's data leak site spiked in February 2025, coinciding with Black Basta's site going offline.
Ransomware groups routinely shut down, rebrand, and reemerge under different names. Members of disbanded operations typically join existing groups or form new ones. Black Basta's infrastructure and expertise likely continue operating under different branding. The addition of Nefedov to international wanted lists may disrupt operations but does not guarantee arrest given his alleged connections to Russian intelligence services and his location in Russia.
Blackout VPN exists because privacy is a right. Your first name is too much information for us.
Keep learning
FAQ
Who is Oleg Nefedov?
Oleg Nefedov is a 35-year-old Russian national identified as the leader of Black Basta ransomware. He operated under aliases including Tramp, Trump, GG, AA, kurva, Washingt0n, and S.Jimmi. He was arrested in Armenia in June 2024 but secured his freedom and is believed to be in Russia.
How was Black Basta exposed?
A year's worth of internal chat logs from Black Basta leaked online in early 2025. The chats exposed the group's structure, key members including Nefedov, and the vulnerabilities they exploited. The leaks led to the group going silent and taking down its data leak site in February 2025.
How much did Black Basta steal?
Black Basta targeted more than 500 companies across North America, Europe, and Australia between April 2022 and February 2025. The group is estimated to have earned hundreds of millions of dollars in cryptocurrency from ransom payments.
What happened to Black Basta members?
Ukrainian and German authorities arrested two Ukrainians who worked as password crackers for the group. Security firms believe several former Black Basta affiliates migrated to CACTUS ransomware after Black Basta's site went offline in February 2025.
Is Black Basta still operating?
Black Basta went silent in February 2025 and took down its data leak site after internal chats leaked. Ransomware groups routinely rebrand and reemerge under different names. Former members likely continue operating under different branding or joined existing groups like CACTUS.